AirTags have been a real revolution in the locator market, but they are also controversial due to the inappropriate use that some people are giving them when tracking the movements of others. What should you do if you think an AirTag is tracking you?
Apple Find Network
AirTags gave way to what is known as Apple Find Network. We can say that all Apple devices connect to each other, no matter who owns them, to help locate each other. if you lose your iPad and someone walks by with an iPhone, this iPhone will send the location to your Apple account so you know where the iPad is. That is to say, all Apple devices act as trackers, and all Apple devices serve as antennas for them to locate each other. But there is a device that does this better than any other: the AirTag.

This small circular device has a single function: to always be located. It doesn't have its own connectivity, no Wi-Fi or data, but it will connect to any nearby Apple device so the design can always know where it is. This is its great utility, no more losing your keys, your wallet, or your bicycle. Any object you attach an AirTag to will be discoverableWhether it's close to your iPhone or far away, as long as someone with an Apple device is nearby, you'll be able to see their location.
track people
It is not a device intended to track anyone, only to be used with objects. But then accessories appeared to put them on dogs, and immediately they began to think that with it they could track people, like children... or like adults. There is no good invention without a bad use for it., and that is true with AirTags, because although they are not intended for this, some people are using it to locate other people without their knowledge or consent.
Apple knew that this could happen, and devised the necessary mechanisms so that anyone who was tracked without their consent with an AirTag would be aware of it. You can really be tracked with almost any Apple device, but using a MacBook Pro is too expensive, so it just won't happen. So in this article we are going to focus on the AirTag as an object to track, ignoring the others, but everything is applicable to all.
What happens if you are tracked with an AirTag?
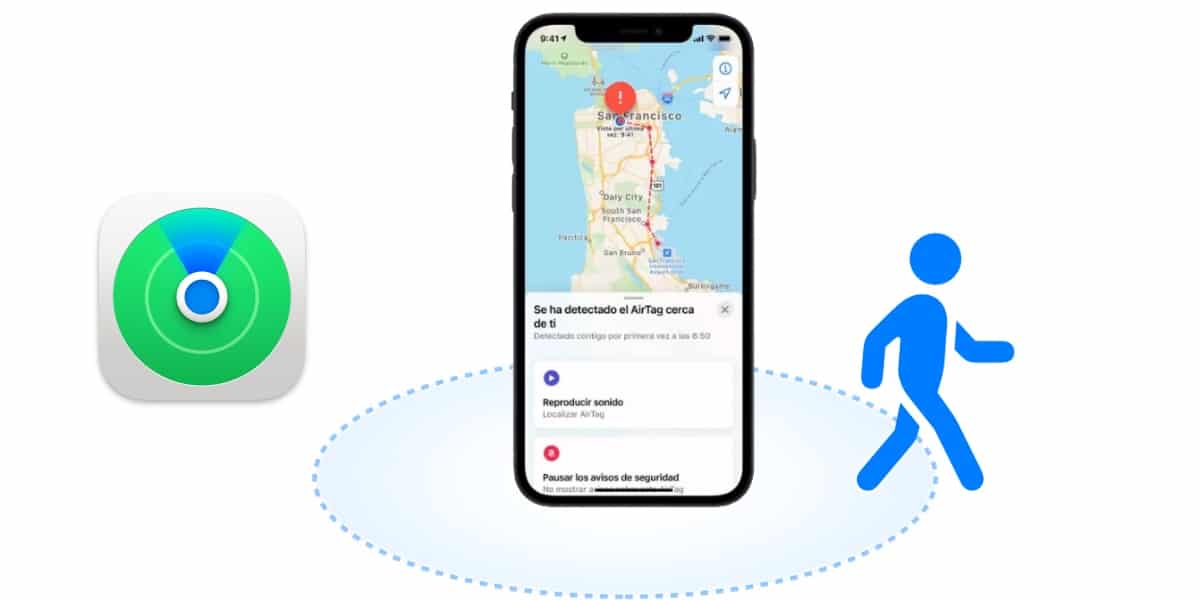
If they put an AirTag in your bag, coat, car or wherever to track you, you will realize it sooner rather than later. When an AirTag spends a long period of time away from its owner and begins to move, it will start beeping for several seconds letting you know that it is with you. If this happens, you will have to follow the sound to locate the small circular object. You may not hear the sound, because it is so hidden, but there are more security mechanisms: you will receive a notification on your iPhone that "An AirTag has been detected near you".
If any of these events occur The first thing you should think about is if you have any object that is not yours. You may be driving someone else's car and the keys are in the glove box, with an AirTag on the key ring. Or that they left you something with an AirTag and they didn't tell you. If this is not the case, then you will have to take active action to locate the possible tracker.
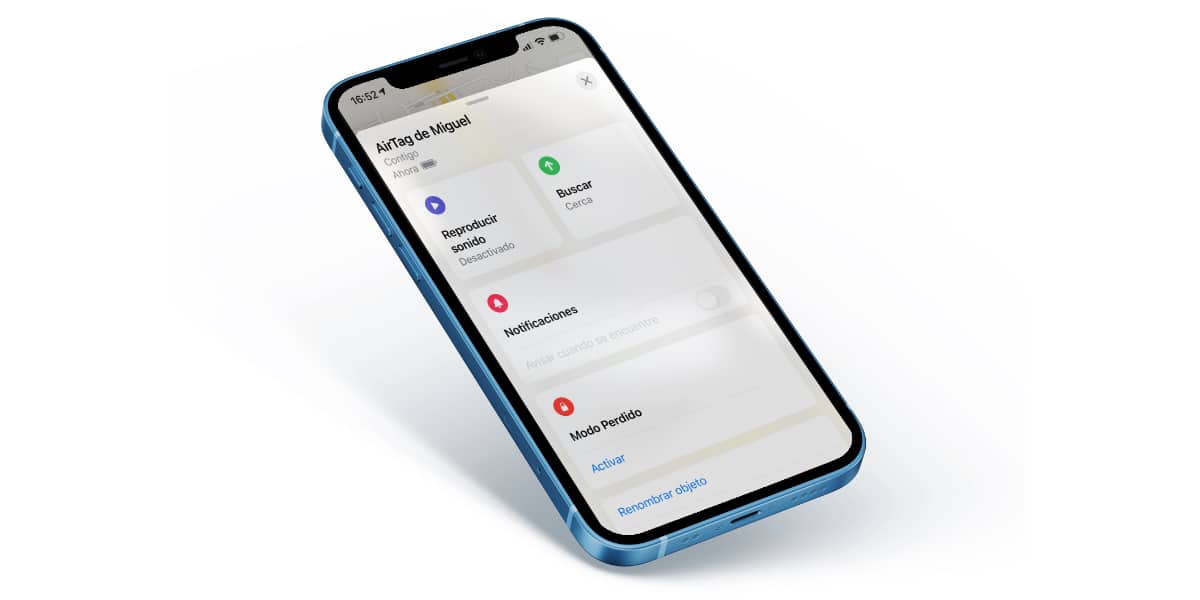
If you heard the sound, look for its source. If you received the notification, click on it. Once you have clicked on “Continue” you can make the AirTag emit a sound to find it. In the event that the object is known and you are not being tracked but it is simply not yours, you can disable notifications for one day. If you think you're being tracked, you can immediately disable the AirTag clicking on “Instructions to deactivate” and you should contact the security forces to notify it.







