Do you want to know how AirTags work? What iPhone models get the most out of it? How can they help you find a lost item? We explain everything to you in this video so that you have it very clear and help you know if you need them or not.
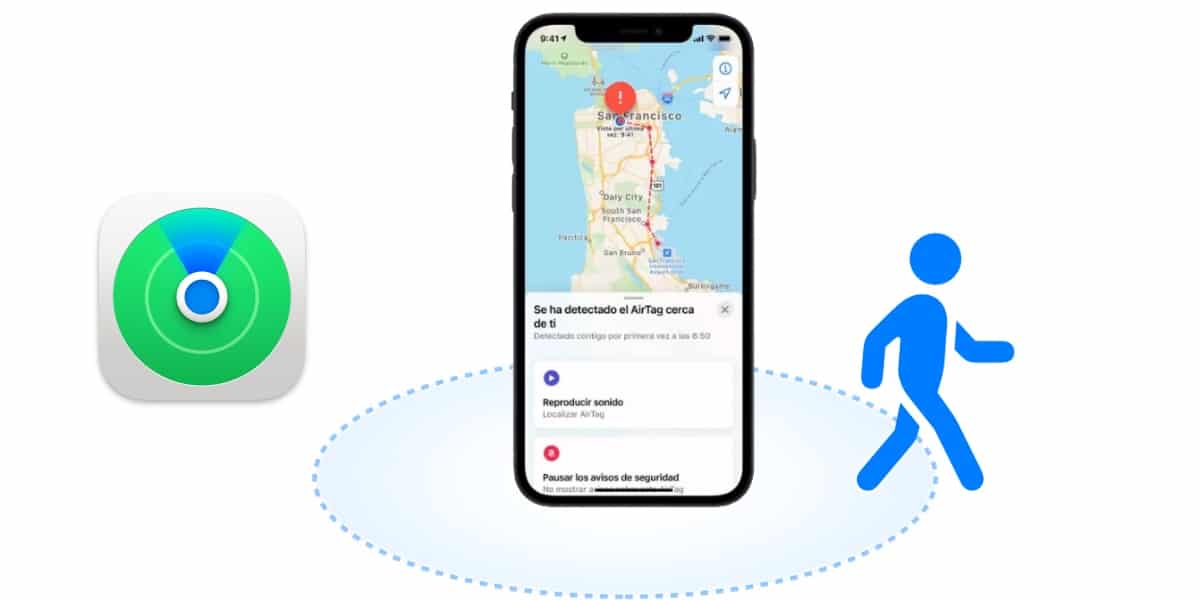
Apple's new locator labels, which we have dubbed "AirTag" as we all expected, come with many new features and differential factors that make them a really interesting product for Apple users. Privacy, a search system integrated into iOS without the need to download applications, the entire worldwide network of iPhone and iPad at your disposal to be able to find your lost object, a more precise search thanks to the U1 Chip that not only tells you if you are close but also indicates in which direction you have to move to find it, integration with Siri to search for your object through voice commands, a lost mode that allows even Android users to identify the owner of the AirTag to contact him if they find it ... these and many other characteristics make these locator tags unique in the market at the moment.
For € 35 you can buy an AirTag, and you can also complement it with countless accessories that are already available from Apple and other manufacturers, plus all those that will arrive in the coming weeks. You can even record it to be completely personalized. Are you interested in this product? Well, in this video we explain all the details that you should know before buying them, not only to know the product well, but to know if it is really worth it for all those functions that it offers you within the Apple ecosystem. Available for reservation from April 23, they can be purchased directly on April 30, also available in physical stores.