With the launch of iOS 15.2 that has been produced recently and officially for both the iPhone and the iPad (in the case of iPadOS 15.2), we have received a series of news and functionalities that have been talked about a few months ago and that do not focus solely on in device optimization.
One of the most anticipated functions is the iOS 15.2 Privacy Report and we are going to teach you everything you need to know to control your data. In this way you will easily know which are the applications and websites that capture this information and where they direct it.
Obviously, in order to take advantage of the new features of the Privacy Report, your iOS or iPadOS device must be updated to version 15.2. For this, you will only have to Head to the Settings application and navigate the menu through General> Software Update. This is the fastest way to install the update, known as OTA (Over The Air), however, there is also the possibility of doing a "clean" installation of iOS 15.2 as already we have told you here on more than one occasion. Once you have made sure you have iOS 15.2, you will be able to run the new features of the Privacy Report.
What is the Privacy Report?
It should be noted that users do not have the Privacy Report activated natively in iOS 15.2, by this I mean that you will have to go to activate it, for this you must follow the route Settings> Privacy> Privacy Report and activate this new functionality, at least it is the case in case you have updated to your current version of iOS 15.2 from a longer version.
In short, the Apple Privacy Report for applications has been designed in order to offer us a complete vision of how the applications that we use regularly treat our personal data. In the report we will find information regarding the frequency with which the applications use the permissions that we have granted them, as well as access to the device's sensors. In the same way, the network activity of each application and each website that we have visited through Safari (or other browsers) will be broken down in a schematic and easy-to-understand way. In this way we will know if the applications take advantage of the permissions that we have granted to share our information with third parties.
- Settings> Privacy> App privacy report
There is a lot of information that it shows us, however, Apple has launched this tool not to actively protect ourselves, but to make ourselves aware of how our data is treated. In this way, we will be able to take control and decide whether or not we want that data processing to be carried out.
The different sections of the privacy report
To show us this information, Apple has decided to differentiate in each of the most important sectors, and bring together this information in an accessible and schematic way. How could it be otherwise, we have different sections or sections for it:
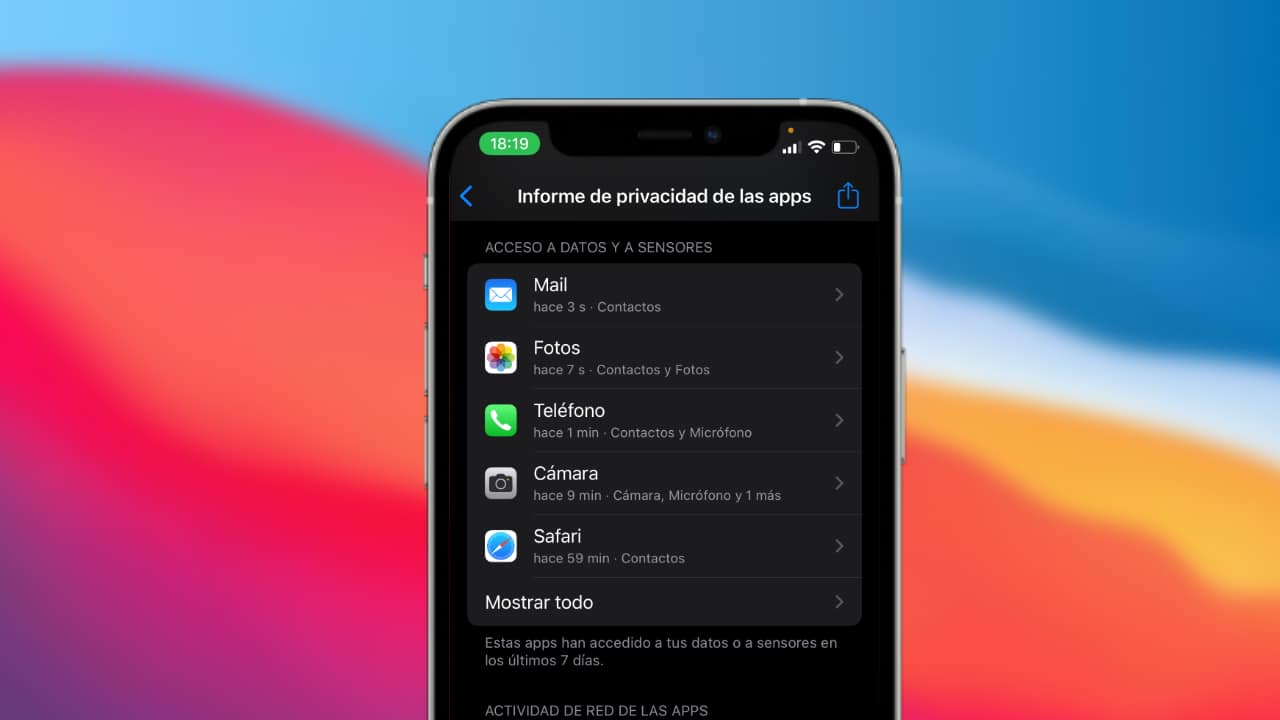
- Access to data and sensors: This section will show us not only when, but also specifically how many times an application has accessed the different data, sensors and specific hardware sections of our device, including: camera, contacts, location, multimedia library, microphone, photo library or screen recording. We will see a summary of the applications that have accessed these elements over the last week (we can click on "show everything" to see all the applications) and if we click on a specific application we will see what information it has accessed and how many times it has accessed it.
- Application network activity: In this section we will be informed about which domains are the ones that contact an application (and vice versa), as well as the date and the exact moment in which said contact took place. This can be the most worrying thing, you will see, for example, how Instagram regularly contacts the Facebook servers to send our information, process it and thus focus the ads in a personalized way. This is not always dangerous, on occasion contacting the domains is necessary for certain functionalities of the application, although its main purpose is to handle the advertising that is shown to us.
- Website network activity: This section focuses on navigation, it will show us the domains with which the websites we visit contact, in the same way as the activity of the applications, but in this case through web browsers. Here we will see how many of the websites we visit regularly contact Facebook or Google, this is essentially to offer us personalized advertising.
Is the privacy report of the apps safe?
The information displayed in the privacy report is stored locally on our device and is not shared even with Apple. In fact, if we deactivate the functionality, the data will be deleted directly from the device and we will no longer be able to view it, the same as would happen if we uninstalled an application, which will make the information related to it disappear.
However, if we want to analyze this data in a massive way or through more complex tools, we can press the "share" button that appears in the upper right corner, in this way we will be able to use the main messaging applications as well as e-mail to send us the report and analyze it as we wish.
As we have said before, in this way what Apple intends is to be transparent with the handling of our privacy. We are used to granting permits, but the companies do not inform us about the actual treatment that is given to our data, We might think that they access the contacts so that we can send them a WhatsApp, but the reality is that they take advantage of access to all that information to create more accurate advertising profiles, or for less ethical purposes, as has been demonstrated on numerous occasions. It is up to you to ensure your privacy, now Apple makes it easier for you.
