Let's talk about software used by hackers to get hold of the stolen images This week, it has already been confirmed that the origin of the images has been the specific attack on the famous iCloud accounts.
In the forum of Anon-IB, popular site where this type of images is published, has been commented and encouraging the use of tools that were used to get the images. In this case it has been carried out with the help of EPPB (acronym for Elcomsoft Phone Password Breaker) and iBrute.
EPPB
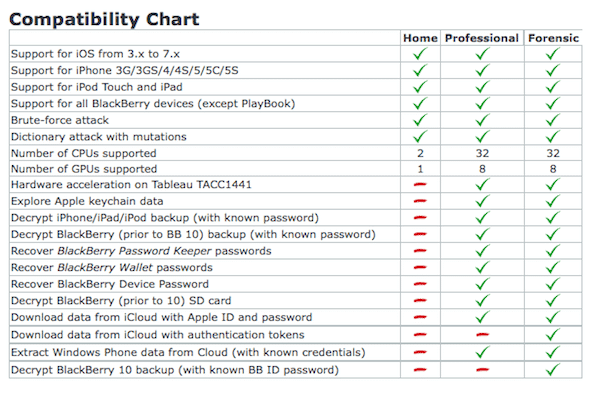
It is software, marketed by a Russian computer forensics company called Elcomsoft, and serves to download the backups located in iCloud of the victims. EPPB desktop application allows content to be downloaded full backup in a single folder, giving intruders access to a large number of data, which would include videos, application data, contacts and text messages.
This program does not require approval from a government agency, It costs around $ 399 for the full version, it has other cheaper versions and even a trial version but can be easily found on exchange sites P2P and its use is easy for the average Anon-IB user.
«Online backups can be extracted by specialists without the need for a terminal. All it takes is have Apple ID and password. These data can be extracted without the consent or knowledge of the owner from the terminal, making EPPB an ideal solution for state security forces and intelligence agencies. » They explain on their website
It is confirmed that this feature works even in Apple accounts with two-step verification enabled.
iBrute
EPPB works in combination with iBrute, a software that cracks iCloud passwords. iBrute is a tool designed by Alexey Troshichev for take advantage of a weak point in the functionality of «Find my iPhone«, which allows you to brute force iCloud passwords.
This software was distributed by Github during the weekend yeThe process was described in the Anon-IB forum as «Use the iBrute script to hack their password and then use the EPPB to download the backups. Post your wins here.»
Consequences
The Cupertino company has declared that it was not an attack on Apple services but rather a specific attack on specific accounts, adding that in none of the cases has any security breach been detected in iCloud or Find my iPhone.
The security breach used by iBrute has been closed by Apple, although it is feared that if hackers downloaded full backups, there is still information to come out, either through leaks or blackmail.

Interesting, I have to buy those programs and learn to do that hahaha.