
Again, user data from at least 3.400 websites including Fitbit, Une and up to 1Password, have been exposedThis time, due to a Cloudflare security flaw, it is recommended to immediately change the access passwords.
User data from more than 3.400 websites have been filtered and cached by search engines as a result of a security bug in Cloudflare, a content distribution network that is used by thousands of websites. For months, websites like Uber, Fitbit or the dating site OKCupid among thousands, have been affected. 1Password also uses Cloudflare, however the company claims that thanks to its end-to-end encryption, its customers' data has not been exposed.
A security flaw that exposes the data of hundreds of thousands of users
The security and privacy of our personal data is something that concerns more and more people every day. More and more personal data that we store in "the cloud" and to which anyone could have access, in most cases, just by knowing our username and password. Hence linformation published today is particularly serious, both qualitatively and in terms of the volume of users it could affect.
According to posted ArsTechnica, Google security researcher Tavis Ormandy discovered that a security flaw in Cloudflare, the content distribution network that is used by millions of websites, has allowed user data from more than 3.400 websites to be leaked. and stored in the cache of search engines.
The service used by 5,5 million websites may have leaked passwords and authentication tokens.
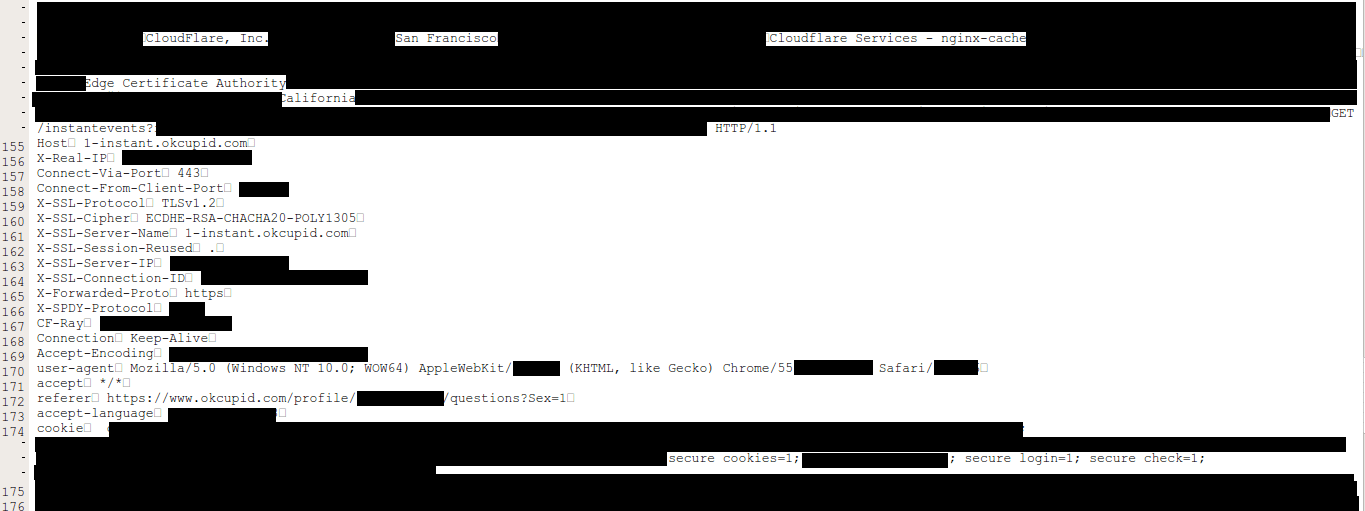
A sample of the data Ormandy saw. This is a private message from the dating site okcupid | IMAGE: ArsTechnica
Among those affected websites are such popular firms as Fitbit or Uber, as well as 1Password, which, however, has already stated that its users' data remains safe thanks to end-to-end encryption.
We've seen encryption keys, cookies, passwords, POST chunks, and even HTTPS requests for other top cloudflare-hosted sites from other users. Once we understood what we were seeing and the implications, we immediately stopped and contacted cloudflare security.
Cloudflare admits the flaw, but could be underestimating its severity
Cloudflare has already admitted that the security flaw has indeed occurred, but both Tavis Ormandy and other security researchers believe that the company is underestimating the severity of the incident. An post Posted on the company's blog under the title "Incident report on memory leak caused by Cloudflare parser bug", Cloudflare acknowledges that the breach was serious, but also notes that there is no evidence that the bug has been exploited.
The error was serious because the leaked memory could contain private information and because it would have been cached by search engines. We have also not discovered any evidence of malicious exploits of the bug or other reports of its existence.
Ormandy was quick to offer a professional to the company's statements stating that the post published by Cloudflare offers excellent "postmortem" analysis but at the same time "severely reduces risk to customers."
It is recommended to change passwords
Ryan Lackey, another prestigious security researcher, agrees with Ormandy's statements, stating that, Although the probability of passwords being exposed is low, that risk exists, so users are encouraged to change them.
Google, Bing, Yahoo, and other search engines have already been clearing the cached data, hence the facts have now been made public, but ArsTechnica notes that some cached data still remains.