
We often say that iOS devices are safe and one of the main reasons we give is that iOS is a closed operating system. Most security problems that affect an iPhone, iPod Touch or iPad affect devices that we have Jailbroken because by doing so we have opened a door to these types of problems. But those who are against Jailbreak for security have to know that no system is 100% safe, as a new Trojan called AceDeceiver which affects users in China even if your device has not been jailbroken.
El malware has been discovered by Palo Alto Networks and it is currently affecting users residing in China. AceDeceiver infects iOS devices taking advantage of FairPlay glitches, Apple's DRM system. According to Palo Alto Networks, the Trojan uses a technique called "FairPlay Man-in-the-Middle" that has been used in the roast to be able to install pirated applications using fake iTunes software.
AceDeceiver takes advantage of FairPlay
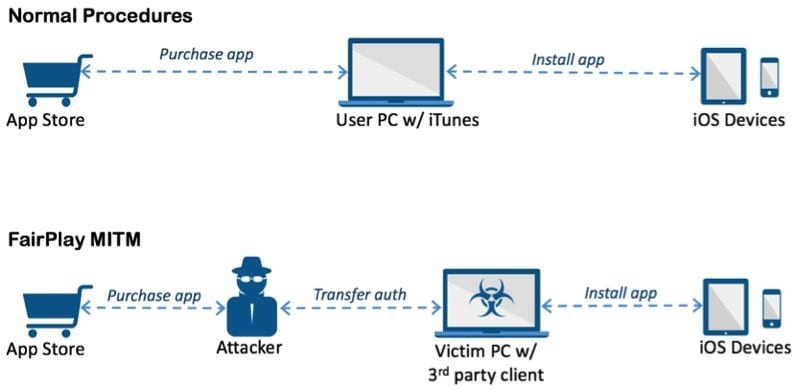
Apple allows users to purchase and download iOS applications from its App Store through the iTunes client on a computer. Computers can be used to install applications on iOS devices. IOS devices will ask for an authorization code for each installed application to verify that the application has actually been purchased. In the MITM FairPlay attack, attackers buy an application from the App Store, then intercept and save the authorization code.
They developed PC software that simulates the resident iTunes client and tricks iOS devices into believing that the app has been purchased by the victim. At that point, the user can install applications that they have never paid for and the creator of the software can install potentially dangerous applications without the knowledge of the user.
From July 2015 to February 2016 three applications were uploaded to the App Store that contained the AceDeceiver code. They were published as wallpaper apps, when they actually provided an authorization code to attackers that they could use in AceDeceiver attacks.
There is a Windows application called «Aisi Helper» which is supposed to offer services like backup and cleaning that has been installed by users from China. This application installs malicious applications on the devices that connect to the computer, offering a third-party App Store with free content as a hook. The third-party App Store asks users to enter their Apple ID and password and that information ends up on AceDeceiver's servers.
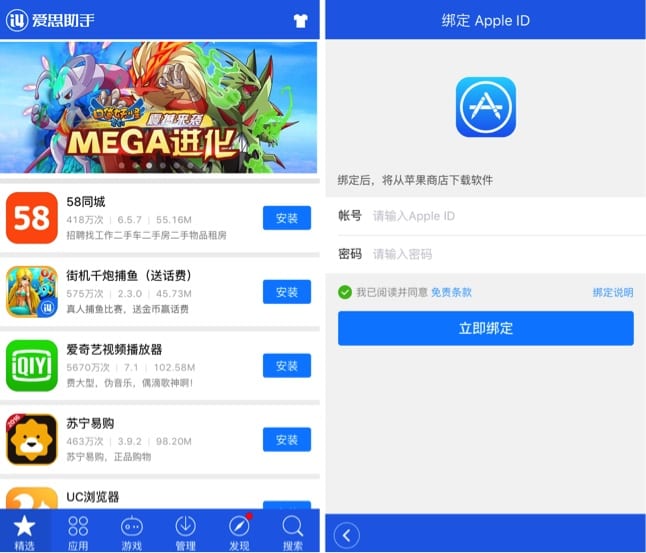
An AceDeceiver app showing an unofficial App Store
Apple removed the apps in February, but the attacks are still possible because the attackers still have the authorization code. AceDeceiver only affects users residing in China, but Palo Alto Networks believes that this Trojan or another malware similar can be extended to other countries. The problem has not yet received a security patch and could be present in older iOS versions that are no longer supported, such as the iPhone 4. In any case, if the problem is serious, Apple will probably release an update just to correct the fault.
In order to work, AceDeceiver currently requires users to download the Aisi Helper Windows application and install it on their computer before the malware can infect iOS devices. Once again, the Importance of only downloading software from official sources and that all that glitters is not gold. This is just as important or perhaps more important on jailbroken devices, but in this case downloading tweaks and applications only from trusted repositories, such as BigBoss (although there was a case where it was hacked and we can never be 100% sure about these things). There are times when common sense can be the best antivirus.

I always use "FairPlay Man-in-the-Middle" in the roast, it is more tender and juicier xD
Hahaha
And don't forget the potatoes and the wine