Apple doesn't forget about its old devices. We found one more proof yesterday, with the launch of iOS 12.5.5, a version intended for all iPhones and iPads that They stopped updating with the release of iOS 13.
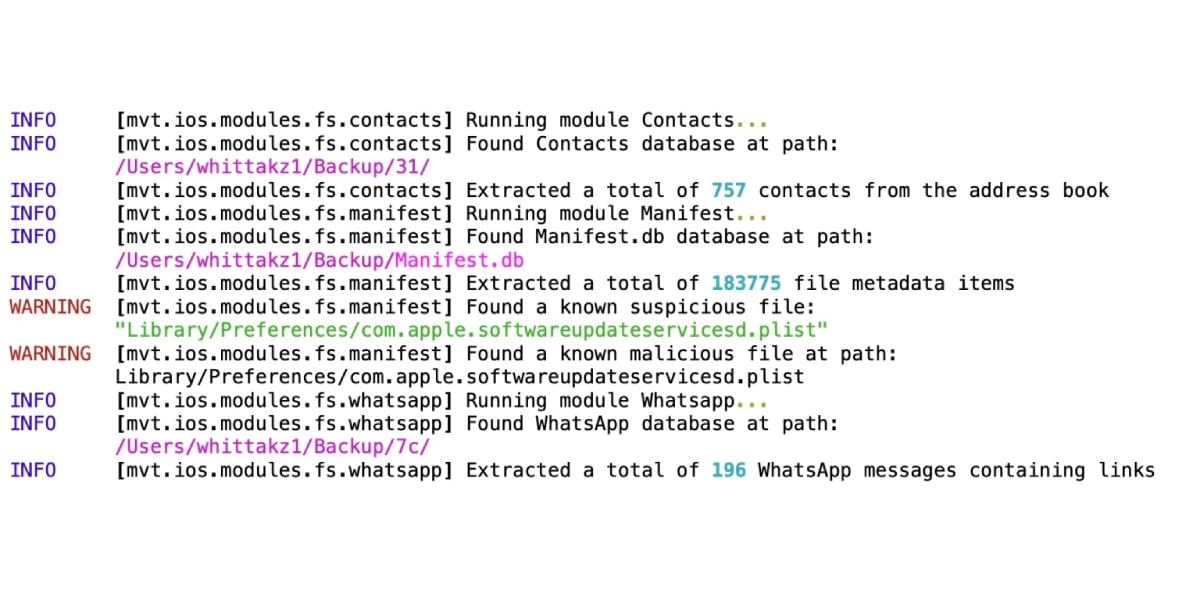
This new update patched three vulnerabilities considered zero day, including one that was probably exploited by the Pegasus software of the Israeli company NSG Group.
One of these vulnerabilities is related to CoreGraphics. This vulnerability allows attackers execute arbitrary code on a target device via maliciously crafted PDFs.
This vulnerability may have been exploited in practice, according to the support document, which details the security content of the update.
The CoreGraphics vulnerability, which affects models Phone 5s, iPhone 6, iPhone 6 Plus, iPad Air, iPad mini 2, iPad mini 3, and XNUMXth-generation iPod touch, was discovered by Citizen Lab, an interdisciplinary laboratory at the Munk School of Global Affairs at the University of Toronto, who further suggests that NSO deployed the exploit to reinforce its Pegasus malware tool.
In recent months, Citizen Lab has discovered multiple zero-day vulnerabilities related to Pegasus spyware, which allegedly It is used by authoritarian governments to hack and police iPhones and other iOS devices used by journalists, activists, government officials, and other persons of concern.
In August, it was reported that an attack vector called 'ForcedEntry' was used to bypass Apple's new BlastDoor security protocols in iMessages, which allowed the insertion of Pegasus in the iPhone 12 Pro of a human rights activist from Bahrain.
Shortly after making this news public, Apple in September released an update for iOS 14 that solved this bug and blocked the operation of this software.