
Practically every week we know of some cyberattack in which the friends of others, have stolen personal data, including passwords or they have used ransomware to encrypt all the content of the computers and request a password to unlock the content. However, computer equipment they are not the only devices that can be used by friends of others to obtain data, being the Pegasus software. ,
Pegasus is a clear example, a software created by the Israeli company NSO Group to extract data from any smartphone, be it iPhone or Android. There is no operating system that is 100% sure, nor will there ever be. Every operating system is vulnerable. However, if we follow the advice that we show you in this article, we can make it much more difficult for friends of others.
Use a VPN
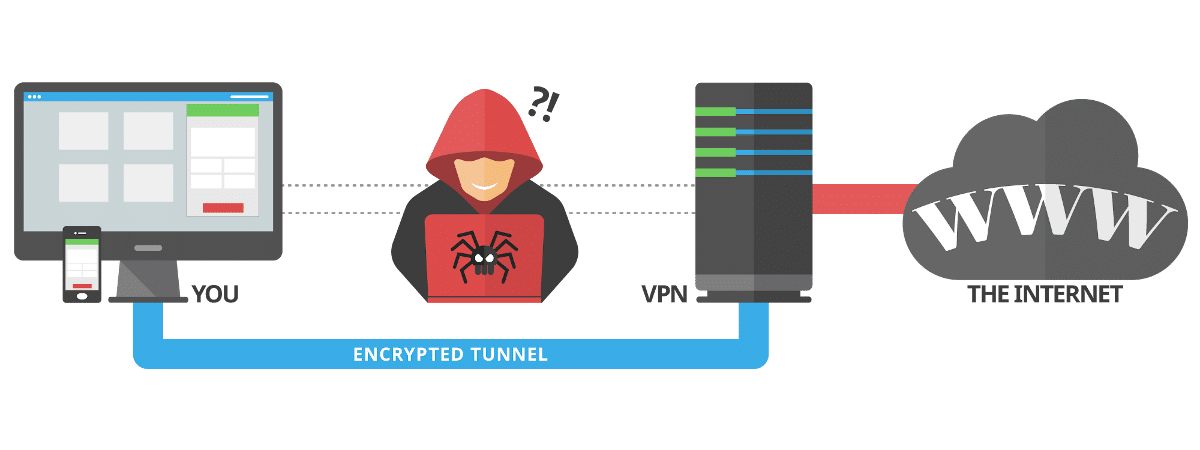
A VPN is a Virtual Private Network that establishes a secure connection between device and server where the information we need is located ... To do this, we must use the VPN free trial that most of them offer us, in order to clear up doubts and check if they really offer what they promise.
When using a VPN, our internet provider (ISP) will never have access to our visit history, it will not be able to know to which pages or to which servers we have connected using our connection.
Paid VPNs, do not store a record that our visits, so they are ideal for not leaving any type of trace when we connect to the internet. Before hiring any VPN service, we must know what are all the services that it offers us and what is the maximum connection speed.
Using free VPNs is not recommended, since each and every one of them trade with our browsing data, since it is the only way to continue offering the service for free. In addition, the connection speed and security they offer us is much lower than that of other paid VPNs.
Do not connect to unprotected Wi-Fi networks

A free connection is very attractive, but just as attractive, tIt is also a source of danger for our smartphone. Being networks without any type of protection, anyone who is in range can connect and monitor all activity on the network to extract data such as passwords.
If we use a VPN, all the traffic that we generate through our smartphone it will be encrypted, so that no person who has access to the traffic generated on the network, will be able to decrypt the content. If you don't use a VPN, these types of Wi-Fi connections are best left untouched with a stick.
Be careful with the Bluetooth connection

The Wi-Fi connection is not the only one with which other people's friends can access our device. Just as it is not advisable to connect to unprotected Wi-Fi networks, we must always avoid using unprotected bluetooth networks, especially in shopping centers, where they have the happy habit of continually sending promotional messages.
Protect access to our iPhone
Although it seems silly, many are the users who do not protect access to your device using a passcode, Touch ID, or Face ID, so that anyone who may have access to our device, even momentarily, has all the content stored inside.
All mobile devices, whether iPhone or Android devices, offer us different methods to protect improper access to its interior. We can never be sure that we will not lose our mobile phone, it will be stolen, we will leave it forgotten in a cafeteria ... Every time we launch a new mobile, the first thing we must do is protect its content.
If, despite the risks of not protecting access to a mobile device, you are still not convinced of the need, it is recommended regularly delete browsing history to reduce the amount of data that other people's friends can access. It is also recommended disable autocomplete to prevent third parties from having access to critical data.
Turn on Find My iPhone
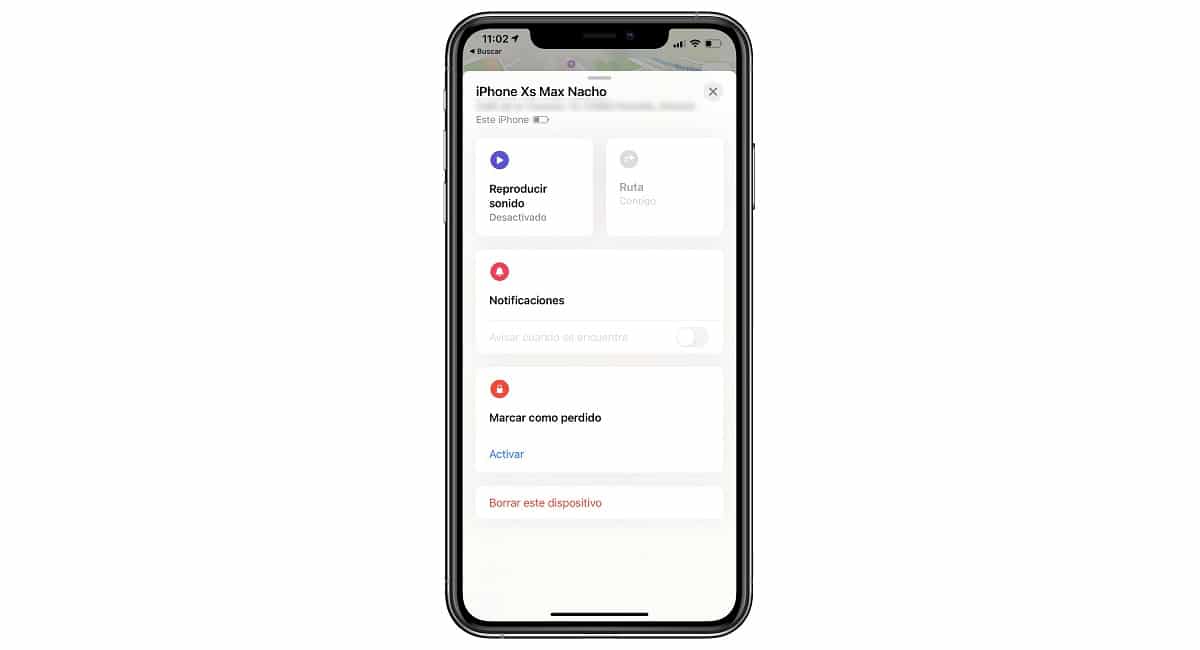
If we are quite forgetful, it is advisable to activate the Find my iPhone function, a function that will allow us to find our device if we have lost it or delete all its content if it has been stolen from us, in order to prevent the friends of others from having access to all the content stored inside.
Always update to the latest version of iOS available
Each new version of iOS introduces new security enhancements in addition to patching the security holes that have been detected since the release of the previous version, so it is always advisable to update as soon as possible to the new versions of iOS that Apple launches on the market.
Other tips

Password protect cloud storage applications
If you use storage platforms to store our important documents, we must make it difficult for other people's friends and activate password protection, Touch ID or Face ID to prevent anyone who accesses our unlocked device from accessing its content.
Turn off Siri on screen lock
It is not the first time nor will it be the last, that iOS bugs allow access some device functions using Siri. This function is available within Settings - Siri and Search.
Don't jailbreak
While less and less popular, jailbreaking is sometimes the only way to get a different experience on iOS. If you like to mess with the jailbreak, it is recommended do not do it on the device you use on a day-to-day basis, since it is an important access door to the entrails of our device.
Use strong passwords
Using the same password makes it easier for us to access services through the internet, but it is a risk if it is not sureIt is short, it does not combine upper and lower case letters and even the odd number.
ICloud Keychain includes a password generator that allows us to create secure passwords that, when stored in the iCloud keychain, do not need to be remembered or written down on paper.
Use two-factor authentication
A tedious security measure that not everyone activates is two-step authentication, since requires an extra step to be able to access a platform, but it offers us an additional layer of security to our password, especially if we usually use the same password for everything, something that is obviously not advisable to do.
Watch out for Phising emails
One of the methods that other people's friends use to try to access our data is impersonate our bank, through an email inviting us to access the platform by clicking on the link included to change the password since a security breach has been detected ...
Summarizing

We should try to be proactive in taking security precautions, not only on our iPhone, but also on our computer equipment, to take measures that allow us to keep our data safe and that it cannot fall into the wrong hands.
