
Apple's two-step verification is a security option that all users should have enabled. By means of this procedure you ensure that only new devices can be added to your account, or access and modify data from it by authorizing that access from one of the devices that we have selected as "Trusted devices". But our devices change, we buy new, we sell old… and this means that a device that was trusted may not be so anymore. We explain below how we can modify this list of devices to always have it updated.

The first thing we must do is access our Apple account, for this we go to the page https://appleid.apple.com and click on "Manage your Apple ID". We enter our access data and since we have the two-step verification activated, we must enter the code that will be sent to us to one of our trusted devices.
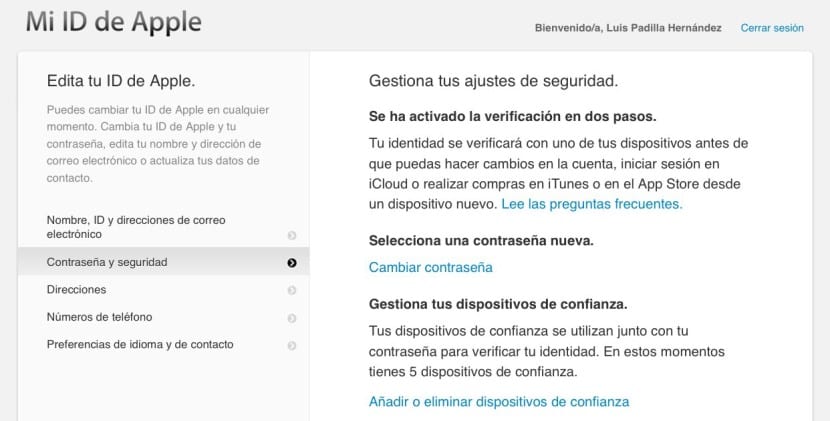
Once inside our account, we must select in the menu on the left the option «Password and security» and there in turn choose the option «Add or remove trusted devices».
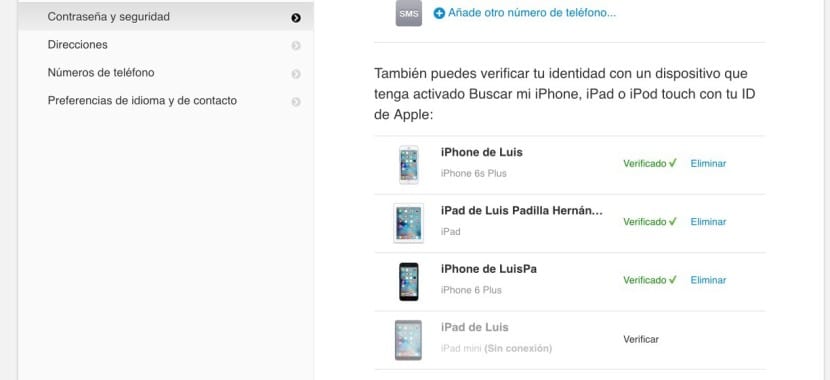
This menu is where all those devices that are associated with your iCloud account will appear. You may see a device that is no longer yours and therefore should not be on the list. By clicking on «Delete» it will automatically disappear and it will no longer be a device that can authorize any changes to your account. You may find devices that are pending to be verified to be part of your trusted devices. By clicking on «Verify» you will be sent a code to that device that if you enter it, it will already be included in your list.
It is important that you have one (or more) phone number as a trusted device. It is the only way that you always guarantee a way to access your account in the remote case you lose all the devices you have. You can always request a duplicate of your SIM and receive the message there to access your account.
