
Project Zero, a Google team specially dedicated to finding security flaws in existing operating systems, has revealed these days one of the biggest attacks that iOS has received since its creation. Up to five security breaches in a two-year period They have been taking advantage to install spyware on our iPhone and iPad.
What are those security flaws? What data have you been exposed to? What devices have been susceptible? How did they work? We are going to explain all the details to you, without any brotherhoods or catastrophies., and in a language that everyone will understand without problems.
Five security flaws
What is a security breach? Operating systems are not perfect, there is no invulnerable system and never will. There are only systems that are more secure than others because they make things more difficult for hackers, but if they are interested, they will always find security flaws that they can take advantage of. These security flaws are "holes" through which hackers can enter our system and doing things that are not allowed, like installing spyware.
In our iPhone or our iPad you cannot install any software that we find, only the one that is in the App Store, and that Apple reviews. Even the software that is in the App Store and that we can install, has limitations and there are functions to which it does not have access, that is what the security that Apple offers its users is based on. But as we said, no software is perfect and sometimes “holes” appear through which malicious applications can slip. These five security flaws that we are talking about today allowed some web pages created by hackers to install spyware on our iOS devices without our knowledge, something that obviously bypasses all Apple security measures.
What web pages are they? They have not been published, but according to the information that has been appearing on the network, these are pages with well-defined political ideologies and expressly created for specific population groups to access, so it is suspected that behind these attacks there would be a state (or several) that what they wanted was to spy on certain groups of their population. What data did they get? Telephone calls, messages, WhatsApp, Telegram, web pages, location ... very valuable information and for which they would have paid large sums of money.
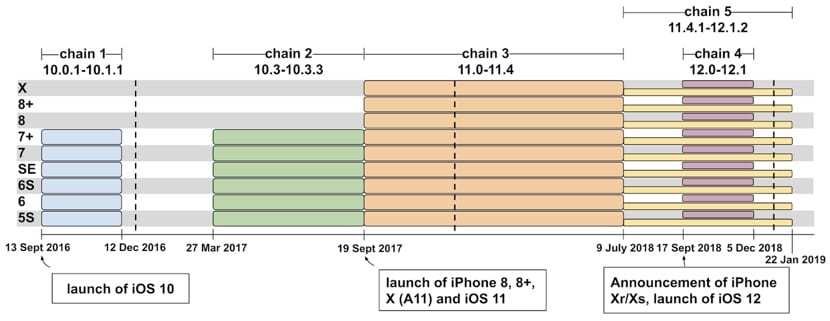
Three of the bugs were already fixed
Project Zero informed Apple of these five security flaws in February 2019, and at that time three of those five flaws were already fixed with the corresponding updates that Apple released at the time. The two bugs that were not fixed, because Apple did not know until Project Zero showed them, took a week to solve with the update to iOS 12.1.4. That is, contrary to what is published in most media, it has not been two years with our iPhone exposed to these attacks, because Apple was patching the bugs as it discovered them.
The longest period of time a bug was active was less than 10 months (“Chain 3”), the rest of the bugs being valid for periods shorter than that due to the updates that Apple was launching, as you can see in the graph above these paragraphs and which shows the dates and versions that solve each of the security flaws.
Solution: always update to the latest version
We will not tire of repeating it despite the fact that many refuse to accept it: having an operating system that supports it through frequent and prolonged updates is the best way to guarantee the maximum possible security. It is important that the response time is minimal, that the update that solves the problem is available as soon as possible, and that it also reaches as many devices as possible. The invulnerable operating system does not exist, but you have to try to stay as close as possible that you can of that unattainable goal.