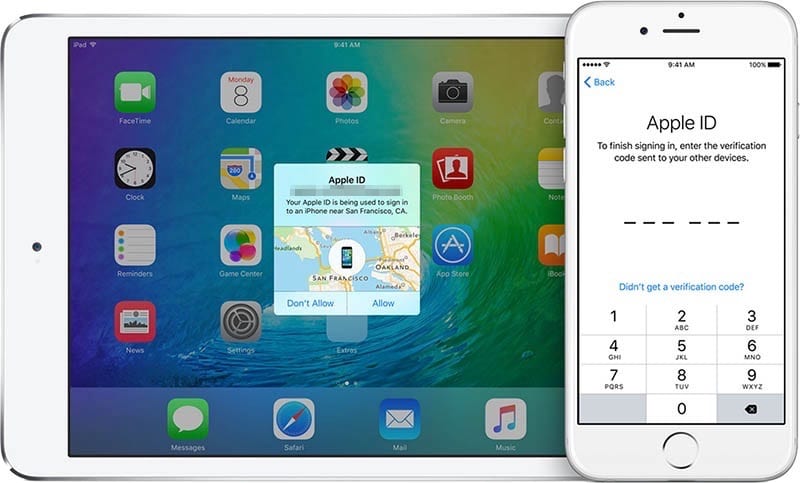
Every day that passes we trust our mobile devices more. In them we keep photos, passwords and all kinds of important information, so the two step verification, a system that, in addition to the password, sends us a security code to a trusted device that we will have to enter in order to access our account.
Currently, once the password has been entered, as long as we have the two-step verification activated, the system will ask us where we want to receive the code, if on a trusted device or via SMS, but the SMS option could have the days numbered. And it is that the National Institute of Standards and Technology (NIST) of the United States posted information from a document that does not recommend the use of SMS as such a verification.
SMS and two-step verification: a story that is ending
According to the study, the problem is that users we can use virtual phone numbers instead of the real ones thus weakening the security of the process. At this time, NIST says that it is still safe to use two-step verification and SMS as long as the phone number it was sent to is real, but it seems that in the future it will not recommend its use whatever the number. to whom the message is sent.
NIST is not an institute that dictates the laws and the decision to follow its recommendations or not has to be made by companies, but they do tend to heed what it says. Most likely, SMS will no longer be offered as an option to access some of the services of Apple and other companies, so in the case of the company headed by Tim Cook, they will have to create applications that can be used by users of Windows, Android, Linux or any other operating system that cannot receive Apple notifications

Two-step verification in apple is so poorly implemented that I would rather have my phone stolen than have to use it. So clearly I say, I had a week to test and it was a real pain in the ass, every time I used any application shared between the iPhone and the Mac, which are practically all of them, it asked me for confirmation. Come on unusable! if all the devices you use are from Apple. Besides, if for any reason you are with one team and you do not have access to the confirmation in the other ... bye you can not do anything. For my part, they can put it where the sunlight does not give them.
Hello, Epidermies. I have been using it for a couple of years and what you say has never happened to me. It only asks me when I log into iCloud from a new browser or when I use an iOS device for the first time.
A greeting.